Configuring your Sophos Firewall
Once your domain, policies, and mailboxes have been migrated you can now configure your Sophos Firewall to relay email to your mailserver. If using Google Workspace or Microsoft 365 and mail does not need to be processed by the Sophos Firewall after Sophos Central Email skip these steps and move on to the next section.
Prerequisite
Prior to configuring your firewall we always recommend creating a backup in case settings need to be reverted. We recommend making these changes during off hours to avoid any major service disruption.
To process inbound email and delivery to your mailserver, this will be done through a DNAT rule on the Sophos Firewall. Before proceeding please take note of the current configuration from your firewall under Email > Policies & exceptions > Policies > smtp Your Policy name.
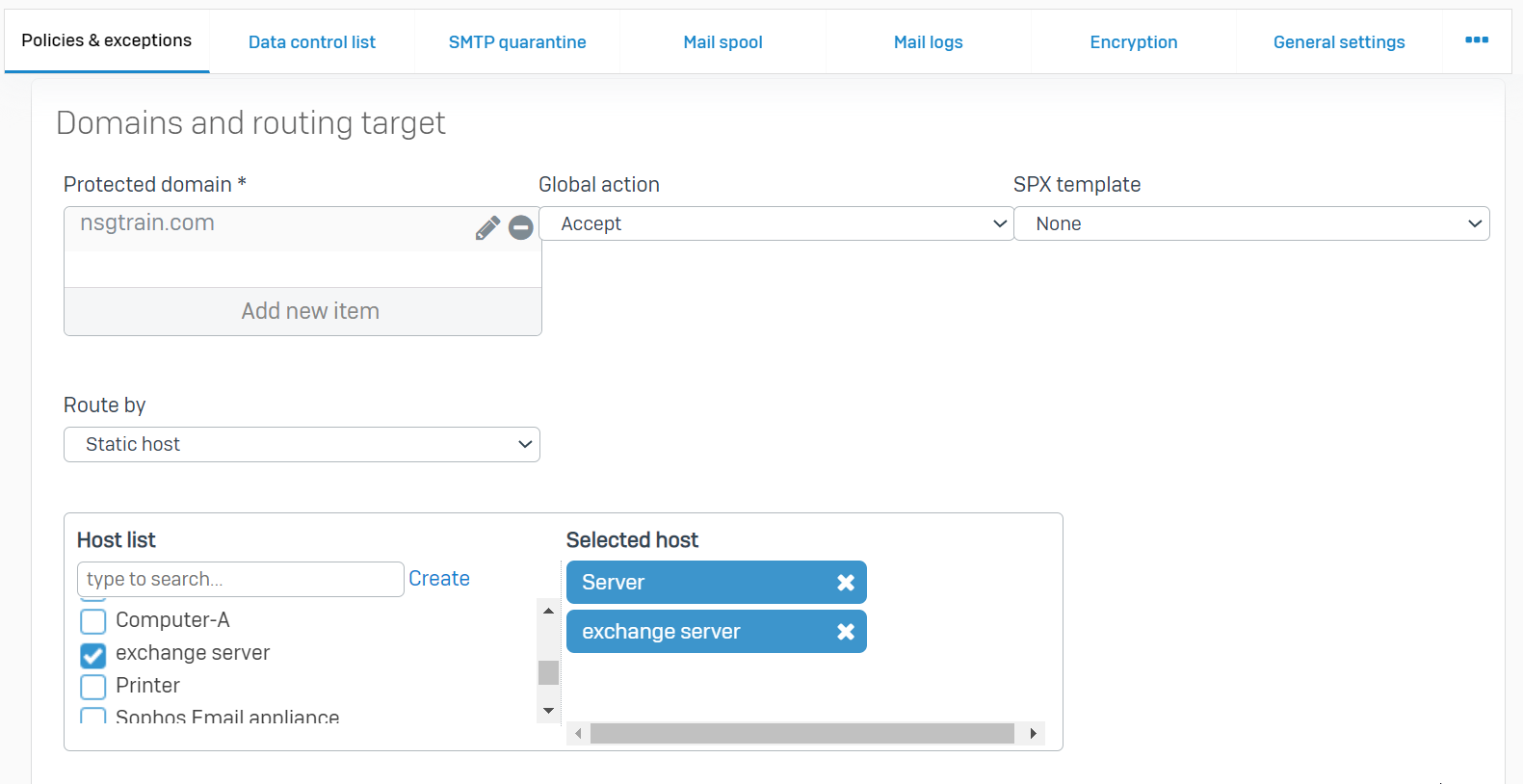
- Protected domain(s), make sure to click the pencil icon to verify all domains listed: eg. nsgtrain.com
- Route By method: eg. Static host
- Host list: eg. Server (192.168.1.25) and exchange server (192.168.25.1)
Create a DNAT rule
If a standard SMTP port (25, 465, 587) is being used for your DNAT rule, rule #1 can be skipped, however please follow the alternative instructions below in step 2 to avoid mail disruption during the transition. If emails for “exampledomain.com” needs to go to a different internal mailsever, then ensure a unique external port for translation is used for every unique DNAT rule. If the same internal mailserver is used in both SMTP policies (or domains), the DNAT rule and ports can be re-used.
-
Optional: If using a non-standard port create a new service port, which is where Sophos Email will deliver and reach the Sophos Firewall for inbound email.
- Go to Hosts and services > Services > Add
- Provide a service name, for example: Sophos Email Delivery
- Choose a destination port that is not currently used on your firewall, it is recommended to use something other than destination port 25, 465, 587
-
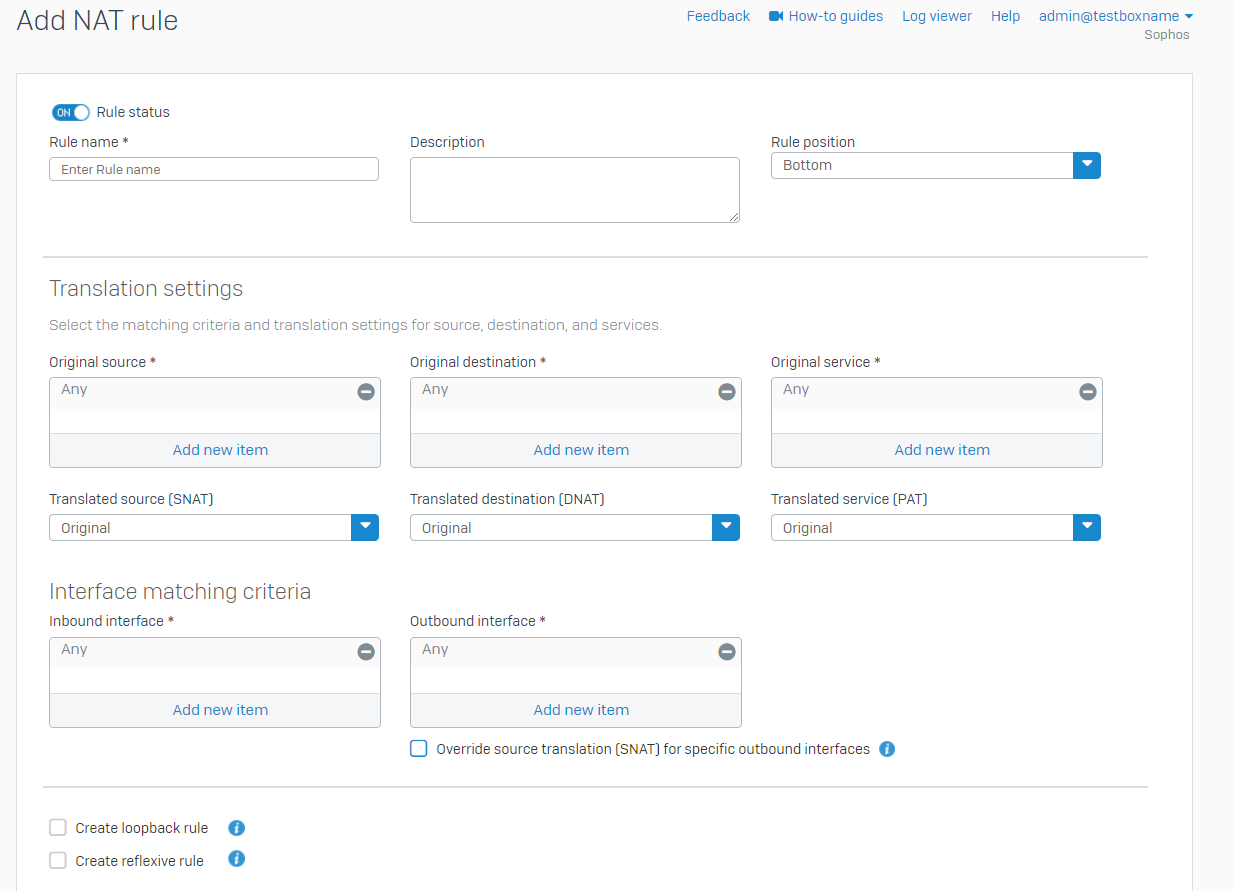
Navigate to Rules and policies > NAT rules > Add NAT rule > New NAT rule. Fill in the details as follows. The following is a recommendation, however can be modified to suit your environment. Anything not listed in the table is not required.
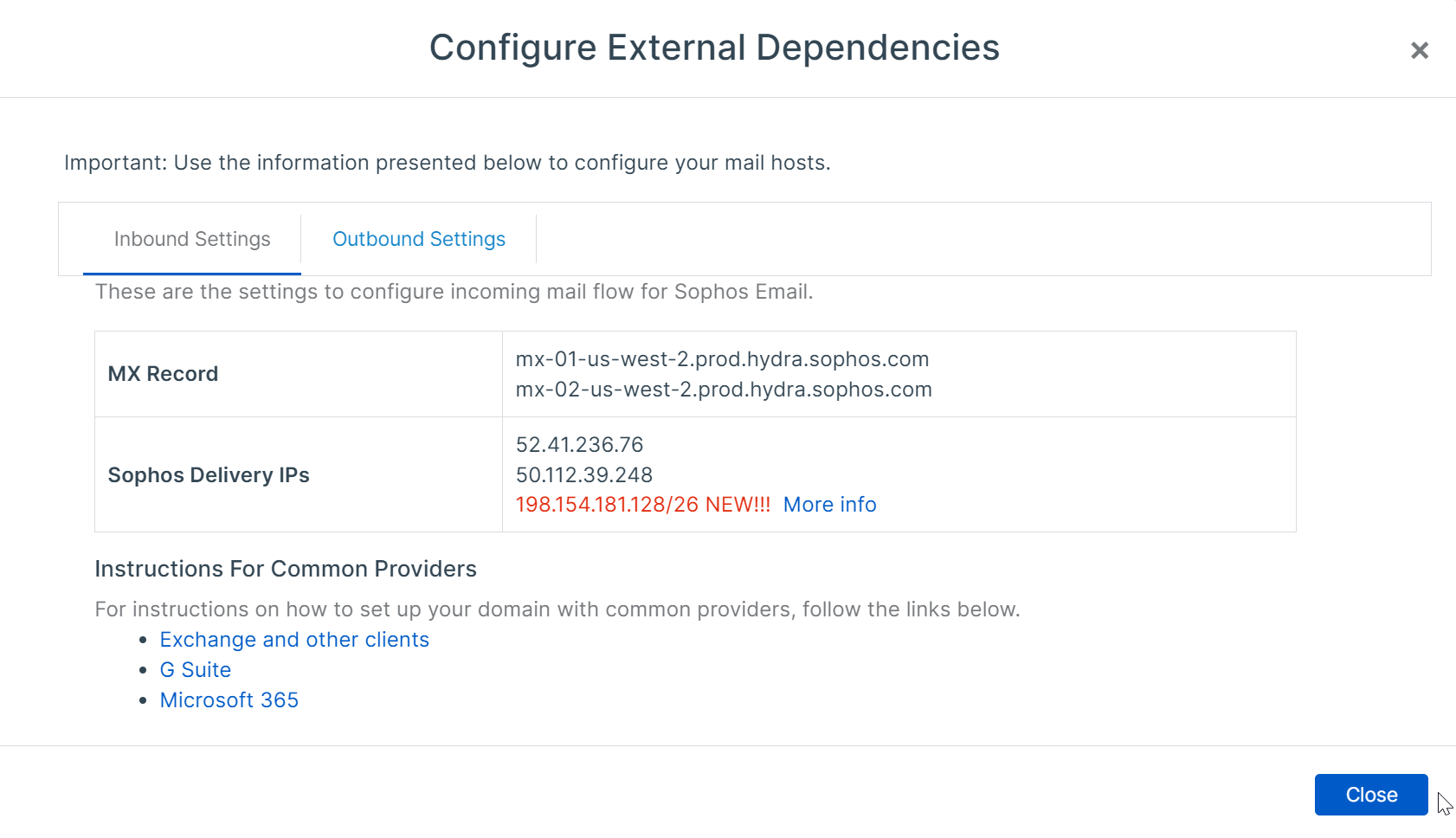
Setting Details Example Rule status Off – prior to updating MX records in final steps, this rule can be toggled on Off Rule name Provide a name for administration purposes Inbound Sophos Email Rule position Recommended to position at the top to avoid conflicts Top Original source Login to central.sophos.com and navigate to Email Security > Settings > Domain settings/status > Configure External Dependencies.
Enter all the networks and IPs under the
Sophos Delivery IPs*US-west-2 central account:
52.41.236.76
50.112.39.248
198.154.181.128/26Original destination The firewalls WAN interfaces from where it will be accepting inbound email from. #PortB (WAN) Original service The destination port Sophos Email will be delivering inbound email to, from step 1. Sophos Email Delivery (port 1234) Translated destination (DNAT) Your Mailserver location, from the prerequisite steps above depending on the Route By type/
- Static Host: If email is being delivered to multiple mailservers, select Add > IP List > specify each mailserver IP, otherwise the single server name can be selected.
- DNS Host: Select Add > FQDN > DNS hostname
- MX: Resolve the internal MX record for your domain and manually specify the FQDN or IP address(es) it resolves to by selecting Add > Your resolved IPs/FQDNs.
Internal Mail Server Translated service (PAT) If a non-standard port for the original service (not port 25) is used, this will likely be required as your mailserver is likely listening on standard smtp ports (eg port 25) SMTP (port 25) Inbound interface Specify all the interfaces from where inbound emails will be arriving from, this will likely match the interfaces from Original Destination PortB Load balancing method (Advanced settings) – Optional If multiple translated destinations or mailservers are used, the load balancing method can be defined. Round-robin
Health Check, port 25Sample DNAT rule below
-
Select Save once the information has been confirmed.
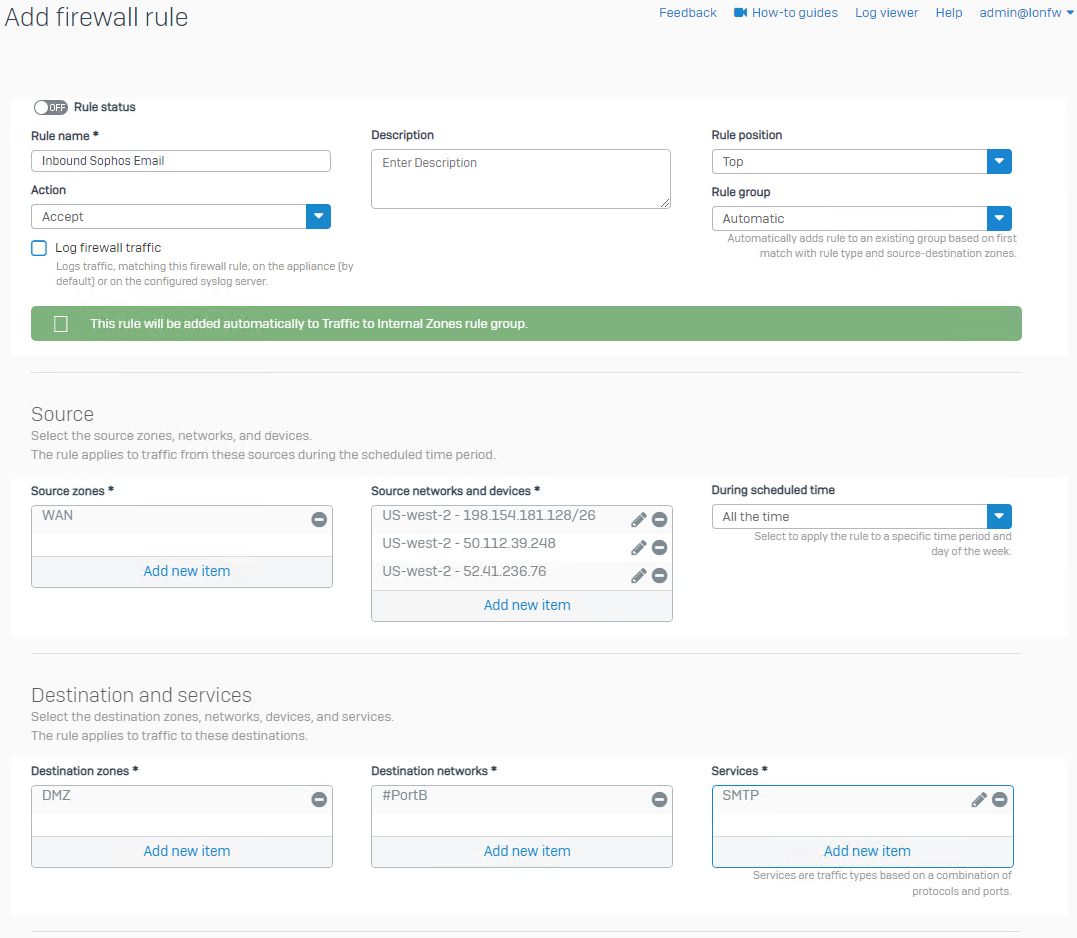
Create a Firewall Rule
Next a Firewall Rule will need to be created to ensure only email originating from Sophos Email is accepted by the firewall. Navigate to Rules and policies > Firewall rules > Add firewall rule > New Firewall rule.
-
Fill in the details as follows. The following is a recommendation, however can be modified to suit your environment. Anything not listed in the table is not required or can be set as default.
Setting Details Example Rule status Off – prior to updating MX records in final steps, this rule can be toggled on Off Rule name Provide a name for administration purposes Inbound Sophos Email Rule position Recommended to position at the top to avoid conflicts Top Source zones All the Firewall Interfaces assigned zone from where it will be accepting inbound email from, likely WAN WAN Source networks and devices Login to central.sophos.com and navigate to Email Security > Settings > Domain settings/status > Configure External Dependencies.
Enter all the networks and IPs under the Sophos Delivery IPs*US-west-2 central account:
52.41.236.76
50.112.39.248
198.154.181.128/26Destination zones The zone where the internal mailserver is located, same as the Translated destination from previous NAT rule created Internal Mail Server is located in the DMZ zone: DMZ Destination network The destination interface Sophos Email will be delivering inbound email to, same as the “original destination” in the NAT rule #PortB Services rovide the listening ports (services) the Sophos Firewall is accepting inbound email from Sophos Email. In this example, the WAN port is listening for port 1234. TCP port 1234 A sample firewall rule is listed below.