Send remote network's traffic through existing IPsec tunnel to specific hosts
You can send traffic from remote subnets through the IPsec tunnel to specific hosts in the local network.
This example uses a virtual IP address to keep the IP addresses of the local hosts private. You must use NAT rules to translate the virtual IP address in the incoming traffic to the local hosts' IP addresses.
Overview
The article is based on the following example settings:
- An IPsec connection exists between Sophos Firewall 1 and 2.
-
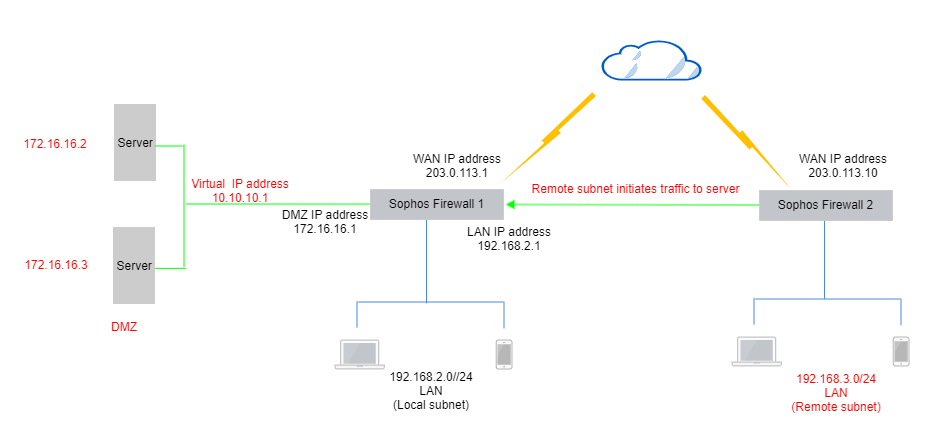
You want to send traffic from the remote subnet (
192.168.3.0) to the local hosts (172.16.16.2and172.16.16.3) through a virtual IP address (10.10.10.1) behind Sophos Firewall 1.For example, you want users to connect securely to an application server, such as a SAP server, that is, the local host.
Network diagram
Add IPsec connection and firewall rules
The settings relevant to this article are as follows:
In Sophos Firewall 1
Route-based IPsec connection
See the following example route-based VPN connection:
- Set Connection type to Tunnel interface.
- Set Gateway type to Respond only.
- Set Local subnet to Any.
- Set Remote subnets to Any.
Assign an IP address to the XFRM interface
- Go to Network > Interfaces.
- Click the vertical blue bar next to the physical interface you specified as Listening interface in the IPsec configuration.
- Click the XFRM interface (example:
xfrm1). - Enter an IP address for the interface.
- Click Save.
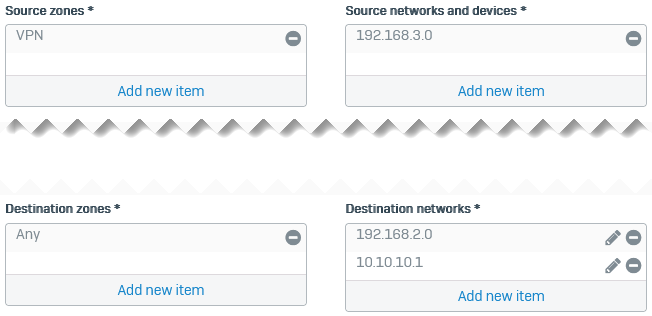
Inbound firewall rule
See the following example inbound firewall rule:
- Set Source zone to VPN.
- Set Destination zone to Any.
- Set Source networks and devices to
192.168.3.0. -
Set Destination networks and devices to the following:
192.168.2.010.10.10.1
In Sophos Firewall 2
Route-based IPsec connection
See the following example route-based VPN connection:
- Set Connection type to Tunnel interface.
- Set Gateway type to Initiate the connection
- Set Local subnet to Any.
- Set Remote subnets to Any.
Assign an IP address to the XFRM interface
- Go to Network > Interfaces.
- Click the vertical blue bar next to the physical interface you specified as Listening interface in the IPsec configuration.
- Click the XFRM interface (example:
xfrm2). - Enter an IP address for the interface.
- Click Save.
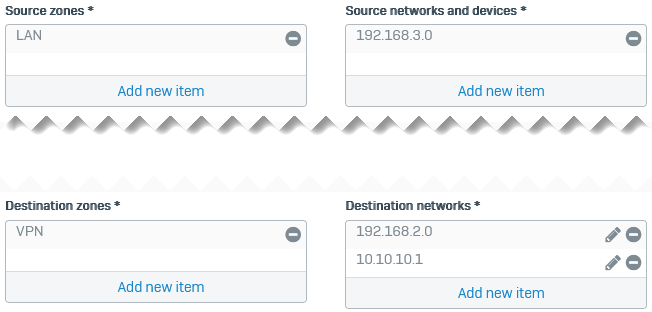
Outbound firewall rule
See the following example outbound firewall rule:
- Set Source zone to LAN.
- Set Destination zone to VPN.
- Set Source networks and devices to
192.168.3.0. -
Set Destination networks and devices to the following:
192.168.2.010.10.10.1
Add routes
You can configure static, SD-WAN, and dynamic routes. This example uses SD-WAN routes.
In Sophos Firewall 1
- Go to Routing > SD-WAN routes.
- Select IPv4 and click Add.
- Enter a name.
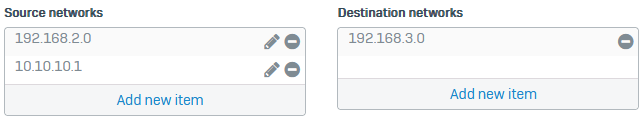
-
Set Source networks to the following:
192.168.2.010.10.10.1
-
Set Destination networks to
192.168.3.0.
- (Optional) Select a service, the application objects, and users and groups.
- Under Link selection settings, select Primary and backup gateways.
- Click the drop-down list for Primary gateway, click Add, and configure a gateway for the XFRM interface (example:
xfrm1_gw1). -
(Optional) Select Route only through specified gateways.
The firewall then drops the traffic if the tunnel isn't available.
-
Click Save.
To allow ping requests for checking connectivity, go to Administration > Device access, and select VPN under Ping/Ping6.
In Sophos Firewall 2
You must route traffic from the remote subnet to the virtual IP address behind Sophos Firewall 1 through the IPsec tunnel.
In this example, we add an SD-WAN route.
- Go to Routing > SD-WAN routes.
- Select IPv4 and click Add.
- Enter a name.
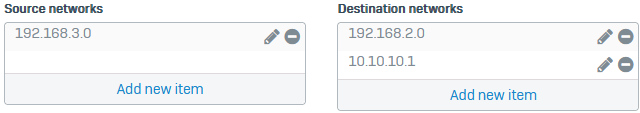
- Set Source networks to
192.168.3.0. -
Set Destination networks to the following:
192.168.2.010.10.10.1
- (Optional) Select a service, the application objects, and users and groups.
- Select Primary and backup gateways.
- Click the drop-down list for Primary gateway, click Add, and configure a gateway for the XFRM interface (example:
xfrm2_gw1). - Select Route only through specified gateways.
- Click Save.
To allow ping requests for checking connectivity, go to Administration > Device access, and select VPN under Ping/Ping6.
Add a DNAT rule in Sophos Firewall 1
Add a DNAT (destination NAT) rule for incoming traffic to translate the virtual IP address (original destination) to the server's IP address (translated destination).
- Go to Rules and policies > NAT rules.
- Click Add NAT rule and click New NAT rule.
- Enter the rule name.
- Set Original source to the remote subnet (
192.168.3.0). - Set Translated source to
Original. - Set Original destination to the virtual IP address (
10.10.10.1). -
Set Translated destination to the local server list object (
172.16.16.2and172.16.16.3).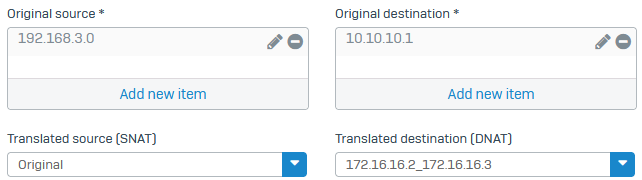
-
Set Load balancing method to Round-robin.
- Click Save.
More resources