Create a remote access SSL VPN with the legacy client
You want to configure and deploy a connection to allow remote users to access a local network. The VPN establishes an encrypted tunnel to provide secure access to corporate resources through TCP on port 443.
Warning
The legacy SSL VPN client reached end-of-life. It doesn't appear for download on the user portal any longer. See End-of-Life for Sophos SSL VPN client.
Users can download the Sophos Connect client instead.
Introduction
You need to do as follows:
- Specify an address range for SSL VPN clients.
- Create a user group for SSL VPN clients and add a user.
- Define a local subnet and remote SSL VPN range.
- Add an SSL VPN remote access policy.
- Add a firewall rule.
- Set up Windows permissions for users to use the SSL VPN client.
- Share the legacy SSL VPN client with users if you already have it. You can't download it from the user portal any longer.
- After installation and importing the connection, check connectivity.
Specify an IP address range for SSL VPN clients
When SSL clients sign in, they're assigned an address from the range specified here. You must use a private address range.
-
Go to VPN and click Show VPN settings.
-
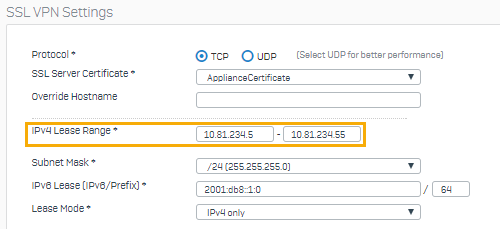
Specify a lease range. If required, you can also update the subnet mask.
-
Click Apply.
Create a user group and add a user
You create a user group for the remote SSL VPN and add a user. The group specifies a surfing quota and access time. Users in the group are allowed unlimited access.
- Go to Authentication > Groups and click Add.
-
Specify the settings.
Option Description Name Remote SSL VPN group Surfing quota Unlimited internet access Access time Allowed all the time -
Click Save.
- Go to Authentication > Users and click Add.
-
Specify the settings.
Option Description Username john.smith Name John Smith Group Remote SSL VPN group -
Click Save.
Create an IP host for local subnet
The local subnet defines the network resources that remote clients can access. You need the IP host for the remote clients to create a firewall rule.
- Go to Hosts and services > IP host and click Add.
-
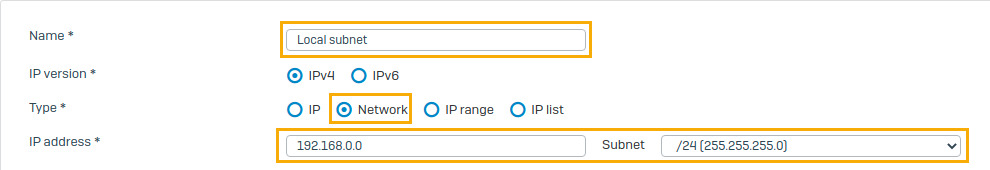
Enter a name and network for the local subnet.
-
Click Save.
Add an SSL VPN remote access policy
You create a policy that allows clients in the Remote SSL VPN group to connect. These users are allowed to access resources on the local subnet.
- Go to VPN > SSL VPN (remote access) and click Add.
-
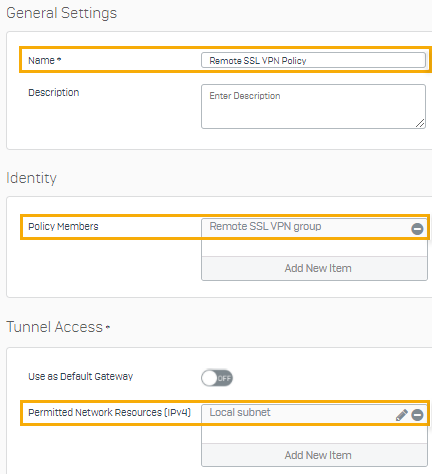
Enter a name and specify policy members and permitted network resources.
-
Click Apply.
Check authentication services
In this example, we set the firewall and SSL VPN authentication methods to local authentication. Sophos Firewall then acts as the authentication server.
- Go to Authentication > Services.
-
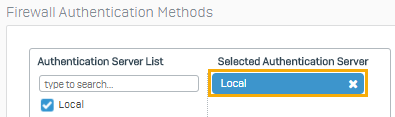
Check that the authentication server is set to Local.
Alternatively, you can select an authentication server, such as the Active Directory server you've configured under Authentication > Servers > Firewall authentication methods.
-
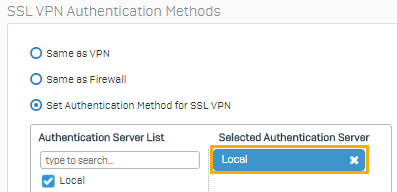
Scroll to SSL VPN authentication methods.
-
Check that the authentication server is set to Local.
Check device access settings
To establish the connection and ensure that users have access to the connection, you must turn on device access for SSL VPN and the user portal.
- Go to Administration > Device access.
-
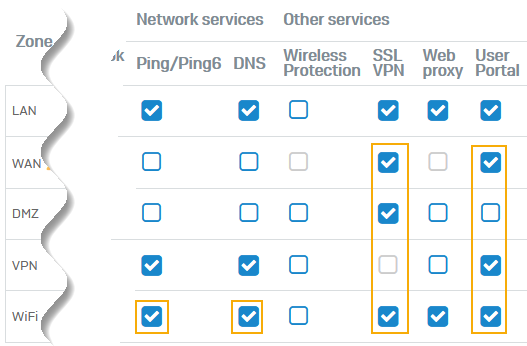
Check access to SSL VPN and the user portal.
-
Click Apply.
Add a firewall rule
- Go to Rules and policies > Firewall rules. Select IPv4 or IPv6 and select Add firewall rule.
-
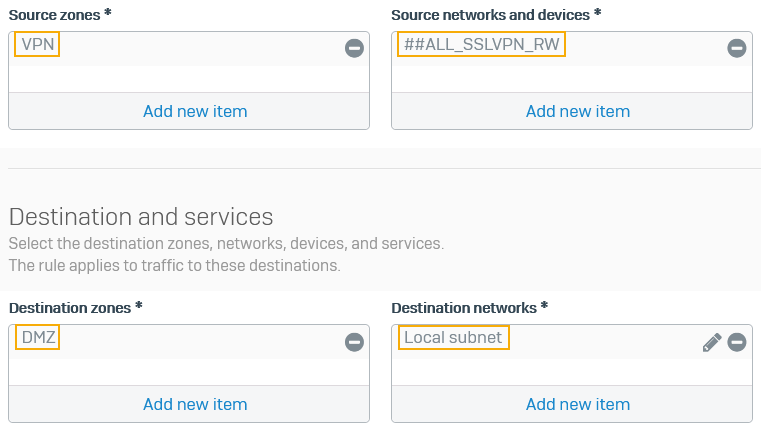
Specify the settings.
-
Click Save.
Windows user permissions required for SSL VPN client
Required permissions for Windows users.
A signed in user who tries to establish an SSL VPN connection needs network operation rights. This allows the SSL VPN client to fully set up the network, for example adding the required routes.
In Windows 7 and 8, network operations are an administrator privilege. You can either assign a local administrator role to users or use the preferred method and add users to the Network Configuration Operators Windows group. Alternatively, users can run the SSL VPN client as an administrator.
To add users to the Network Configuration Operators Windows group, do as follows:
- In Windows, open Control Panel > Administrative Tools.
- Open Computer Management.
- Expand System Tools > Local Users and Groups.
- Click Groups.
- Double-click Network Configuration Operators, and then click Add.
- Enter the username, click Check Names to ensure accuracy, and click OK.
- Click Apply to save the changes.
Deploy the connection
Install an authentication client and connect to the internal network using the VPN connection.
Follow these instructions to deploy the legacy SSL VPN client.
Do the following on the endpoint computer.
-
Log on to the user portal.
Warning
We don't recommend enabling the web admin console on external facing (WAN) interfaces. This could allow hackers to identify the firewall vendor and type easily, and launch a targeted attack. If the user portal isn't being used, we also recommend deactivating this service on WAN interfaces.
To restrict Sophos Firewall user portal and web admin console to local interfaces, go to Administration > Device access, then deselect User Portal and HTTPS from the WAN zone.
If you enable the user portal on WAN interfaces, we recommend you set up two-factor authentication. See Configuring two-factor authentication.
-
Share the legacy SSL VPN client with users if you already have it. You can't download it from the user portal any longer.
- Double-click the client installer file and follow the prompts to finish the installation.
- Start the client and log on using the username and password.
If authentication fails, go to Authentication > Users and check whether the user account has MAC binding enabled. If MAC binding is enabled, disable it.
Check connectivity
Check the connectivity from the endpoint computer and on Sophos Firewall.
- From the endpoint computer, you can check that you've been assigned an IP address from the SSL VPN range configured earlier on Sophos Firewall. In Windows, open Command Prompt and type the following command:
ipconfig
You should see an address in the10.81.234.5to10.81.234.55IP range. - On Sophos Firewall, you can go to Current activities > Remote users to view the traffic. You can also go to Rules and policies > Firewall rules.
More resources