RED operation modes
The RED operation mode defines how the remote network behind the RED integrates into your local network.
All wireless traffic behind REDs that are deployed in a separate zone is sent to Sophos Firewall using the VXLAN protocol regardless of the operation mode.
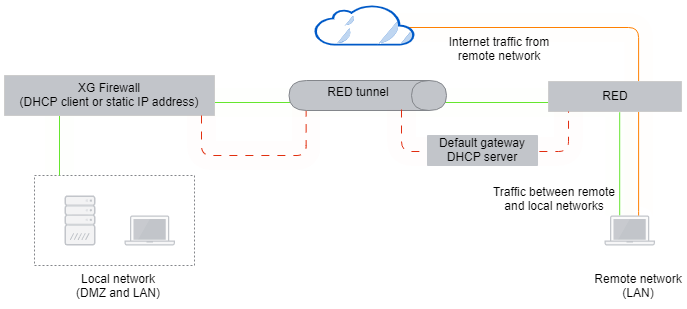
RED can operate in several modes. Sophos Firewall is deployed in your local network and the RED appliance in your remote network. The RED appliance establishes a tunnel with Sophos Firewall. Both have a connection to the internet. Here's an example:
Standard/Unified
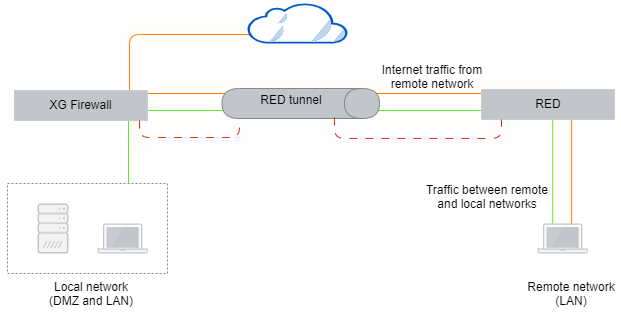
The firewall fully manages the remote network through the RED. It acts as a DHCP server and default gateway.
DHCP can be offered for the remote LAN by the firewall, and the RED may be the only device connecting the LAN to the internet. While another router may sit in front of the RED, there isn't a parallel path around the RED to the internet.
In this mode, the firewall can allow or deny requests as it does for traffic coming from the local LAN. This provides the highest level of security and manageability for remote networks. However, the local network must have sufficient bandwidth to service requests from both its local users and all remote RED users.
Note
Handle VLAN traffic through the Standard/Unified mode if VLAN is deployed behind the RED.
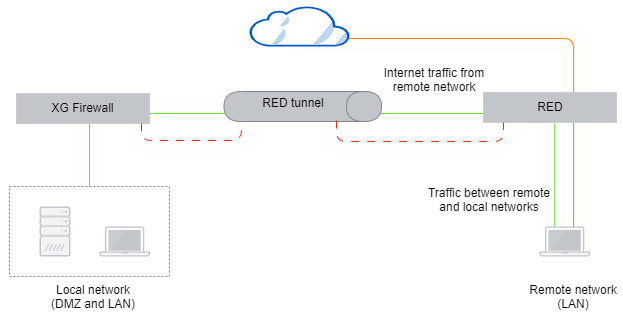
Standard/Split
The firewall manages the remote network and acts as a DHCP server. Only traffic targeted to split networks is redirected to your local firewall. All traffic not targeted to the split networks is directly routed to the internet.
In this mode, the RED masquerades outbound traffic to come from its public IP address. This feature minimizes bandwidth usage over the tunnel and lightens the bandwidth requirements on the firewall, but it also reduces the manageability of the remote network substantially. Traffic to or from the internet can't be filtered or protected from threats. Security can only be applied between the remote and local LANs.
Note
This mode isn't compatible with VLAN tagged frames.
Transparent/Split
The firewall does not manage the remote network. It's connected to the remote LAN and the remote LAN’s gateway and receives an address on the remote LAN through DHCP. Only traffic destined for certain networks transmits down the tunnel. In this case, the RED does not act as the gateway, but it's in-line with the gateway and can transparently redirect packets down the tunnel.
Since the firewall has no control of the remote network, local domains can only be resolved by the remote router if you define a split DNS server. This is a local DNS server on your network that can be queried by remote clients.
In this mode, the local interface of the RED and its uplink interface to your local firewall as well as its link to the remote router are bridged. Since the firewall is a client of the remote network, routing traffic to the split networks the same way as with other modes isn't possible. Therefore, the RED intercepts all traffic. Traffic targeting a split network or split domain is redirected to the firewall interface.
Note
This mode isn't compatible with VLAN tagged frames.