Generate detections (NDR)
You can generate test detections to check that Sophos NDR is correctly set up and working.
The test isn't malicious. It triggers a detection by simulating an event with features typical of an attack. The event is a client downloading a file from a server with suspicious domain and certificate details.
You can run the test from Appliance Manager.
Requirements
Make sure Appliance Manager can access our test server. Configure your firewall to allow TCP traffic to this domain and IP address:
- Domain:
plrqkxqwvmtkm.xyz - IP address:
13.56.99.184 - Port:
2222
Make sure you've included your network traffic in the current port mirroring setup. For help, see the NDR setup pages in Sophos integrations.
Generate a detection
Note
You must access Appliance Manager from a device on the same network as Sophos NDR.
- In Sophos Central, go to Threat Analysis Center > Integrations > Configured.
-
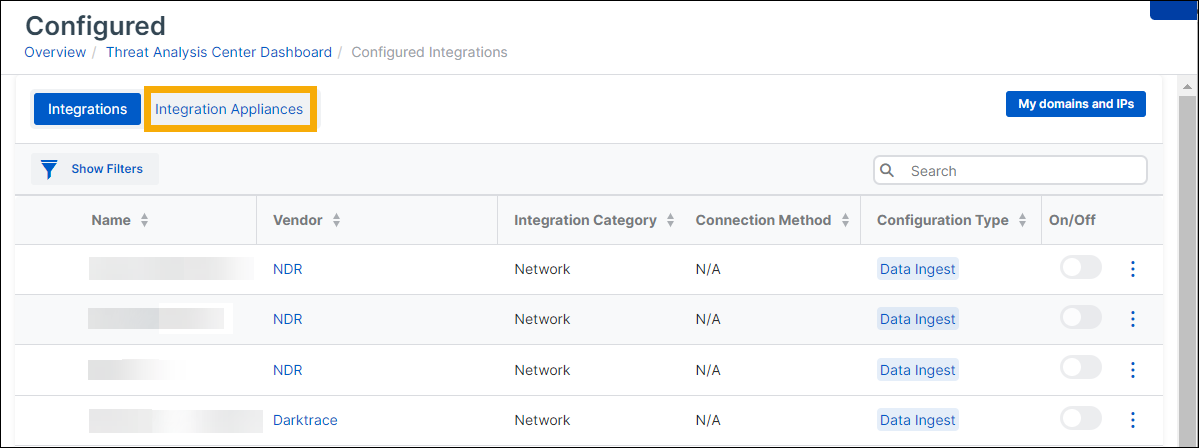
Go to the Integration Appliances tab.
-
Find the appliance. In the rightmost column, click the three dots and select Open Appliance Manager.
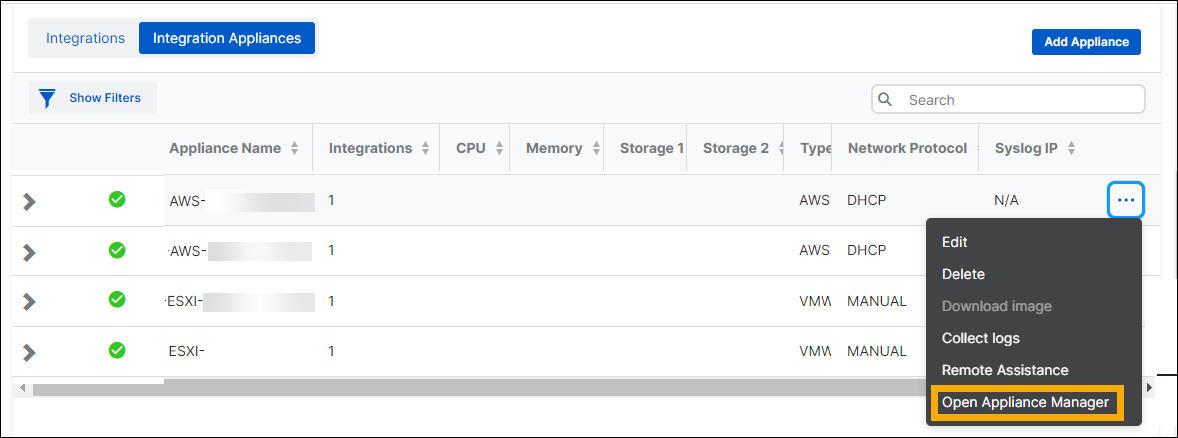
-
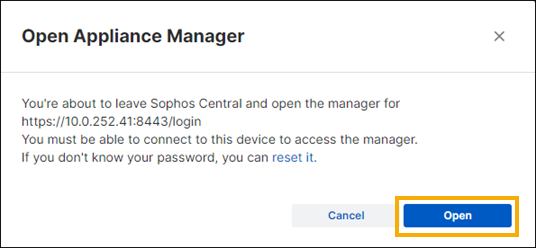
In the confirmation dialog, click Open.
-
On the sign-in screen, enter the username
zadminand your password.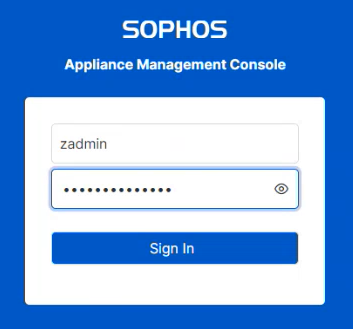
-
In Appliance Manager, select Generate Detections.
-
On the Generate NDR Detections page, click Generate Detections.
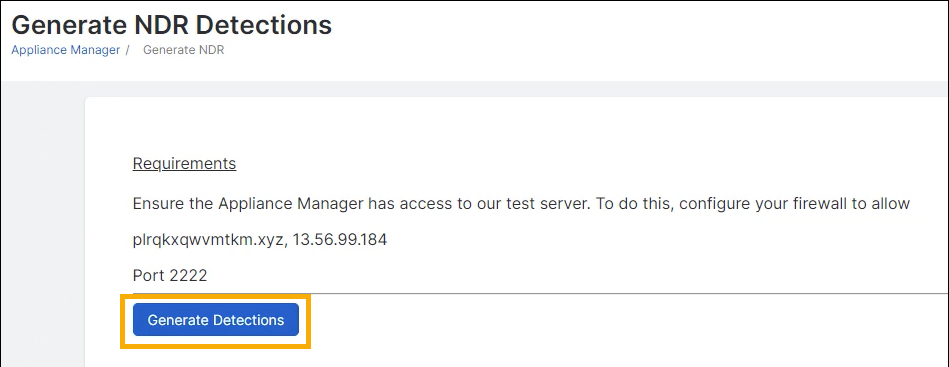
-
When you see a message confirming that a detection is being generated, click OK and wait for ten minutes.
- Go back to Sophos Central.
-
Go to Threat Analysis Center > Detections.
-
On the Detections page, you should see a recent high-risk detection named
NDR-DET-TEST-IDS-SCOREin the list.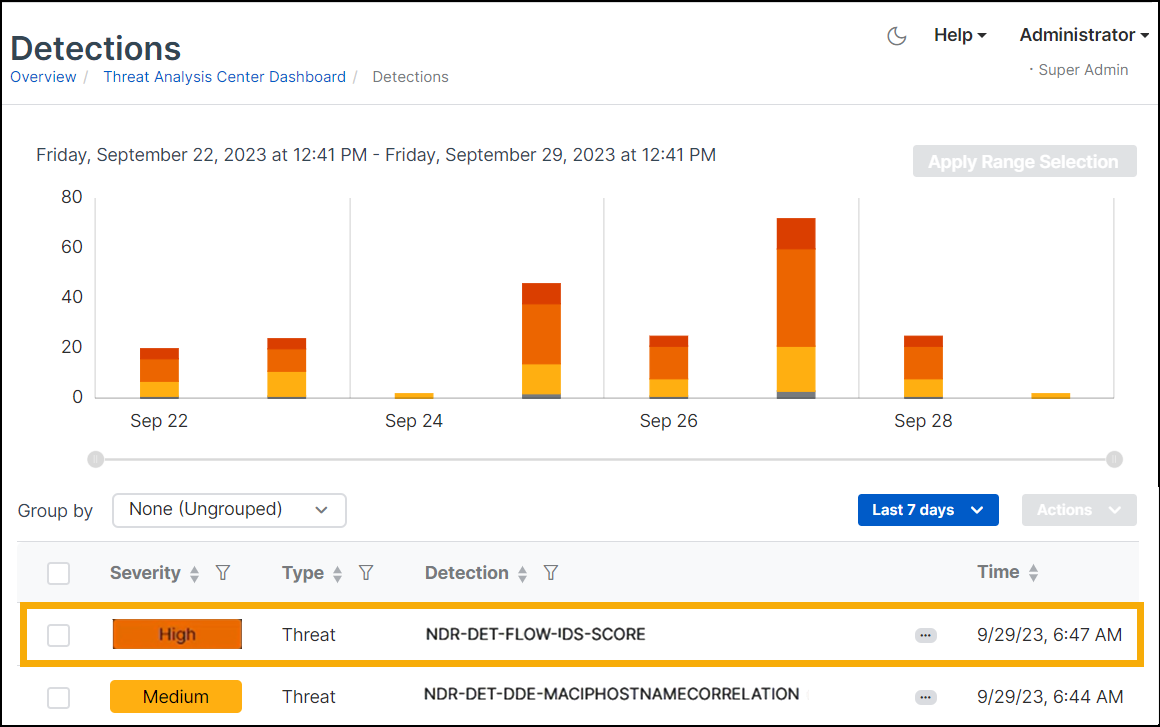
-
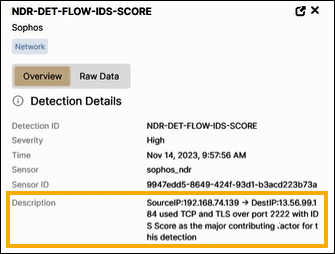
Click
NDR-DET-TEST-IDS-SCOREto open its details.The Description shows a source and destination IP communicating over TCP and TLS on port 2222. It also shows IDS (Intrusion Detection System) as the main contributor to the detection. IDS is a list of blocked certificates.
-
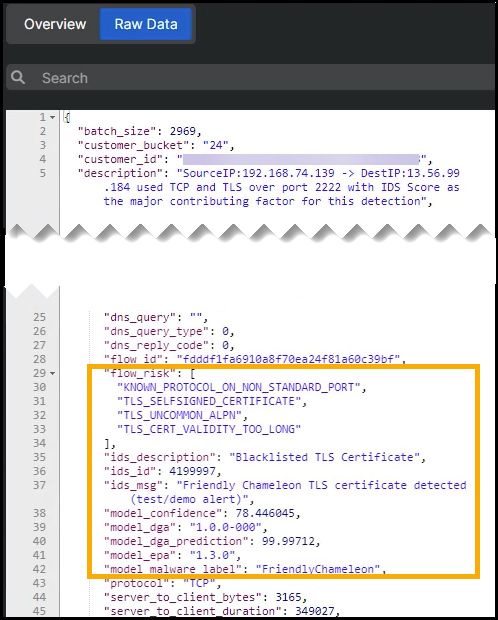
Click the Raw Data tab. The
flow_risksection shows the following details:- Known protocol on a non-standard port
- Self-signed certificate
- Uncommon Application-Layer Protocol Negotiation (ALPN)
- Blocklisted certificate
- High probability that the server domain is generated by algorithm (DGA)
- Indications of a threat belonging to the Friendly Chameleon family.
For information about generating an NDR detection from the command-line interface, see Generate NDR detections from the command-line interface.