Sophos NDR on AWS
You must have the Sophos Network Detection and Response integration license pack to use this feature.
Sophos Network Detection and Response (NDR) detects malicious behavior on your network.
You can integrate Sophos NDR with Sophos Central so that its detections are available for investigation in the Threat Analysis Center.
The integration uses an appliance that receives data and forwards it to the Sophos Data Lake.
The main steps are as follows:
- Check the requirements.
- Create a Sophos appliance. This is based on a CloudFormation template.
- Subscribe to Sophos NDR in AWS.
- Create a stack. You specify the VPC and subnets for NDR here.
- Create a traffic mirror session. This sends traffic to NDR for analysis.
- Edit security groups to allow syslog traffic and give access to Sophos Appliance Manager.
- Set a password for Sophos Appliance Manager.
Appliance Manager lets you monitor and manage the Sophos NDR appliance.
Requirements
To set up Sophos NDR on AWS, you need the following accounts and infrastructure:
- An AWS account.
- A Sophos Central account.
- EC2 instances.
- VPCs, subnets, and availability zones. You can use the ones you already have.
- At least one allocated Elastic IP Address to be used by the NDR management interface.
We support these EC2 instance types:
- c5n.2xlarge
- c6i.4xlarge
- c7i.16xlarge (nitro virtualization)
You must create and save your SSH private key for the AWS account.
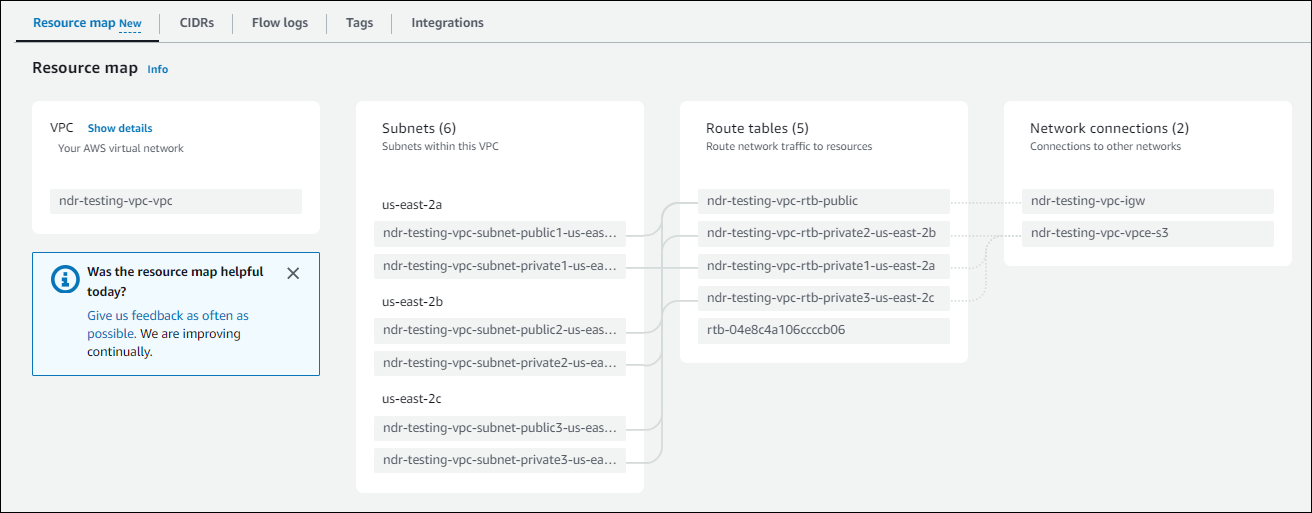
You must have a VPC created in any of the regions of your choice. Here’s an example of a VPC resource map:
Create an appliance
To create and configure a Sophos appliance, create and download a CloudFormation template.
Create the CloudFormation template
To create a CloudFormation template, do as follows:
- In Sophos Central, go to Threat Analysis Center > Integrations > Marketplace.
- Find and click Sophos Network Detection and Response (NDR).
-
On the NDR page, in Data Ingest (Security Alerts), click Add Configuration.
Integration setup steps appears.
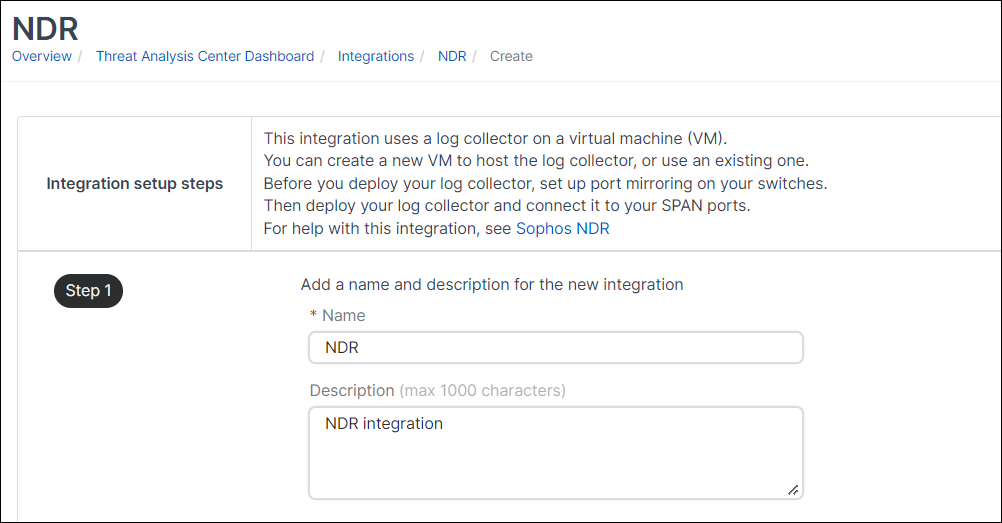
-
In Step 1, enter a name and description for the integration.
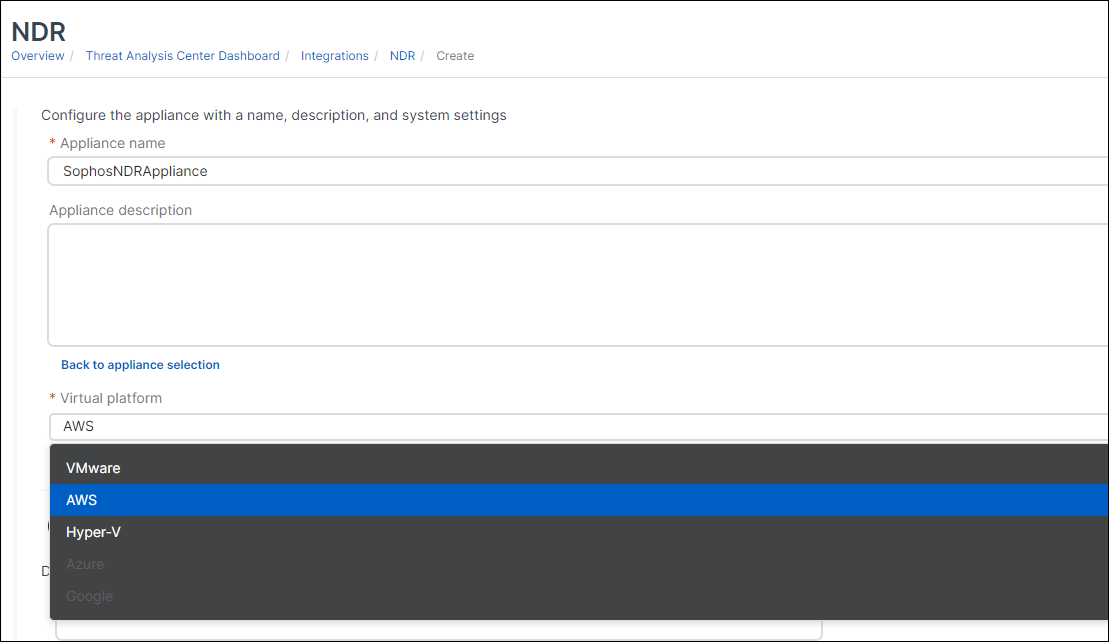
-
In Step 2, create a CloudFormation template (CFT). In Virtual platform, select AWS.
-
Click Save.
A CloudFormation (CF) json file aws_ndr_cf_latest.json is created.
Download the CloudFormation template
To download the CloudFormation template, do as follows:
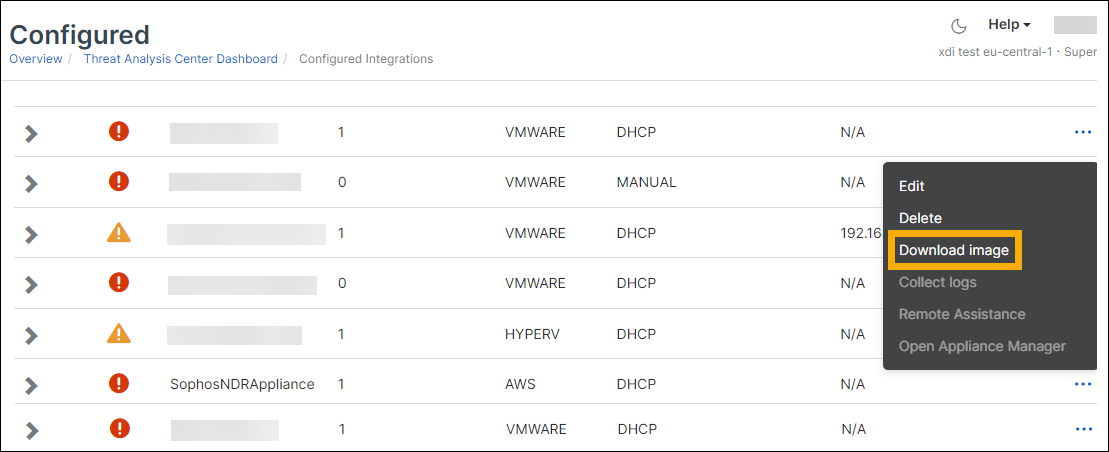
- In Sophos Central, go to Integrations > Configured.
- Select the Integration Appliances tab and find the Sophos NDR appliance.
-
In the rightmost column, click the three dots, and select Download image.
The aws_ndr_cf_latest.json file is downloaded to your Downloads folder.
Subscribe to Sophos NDR
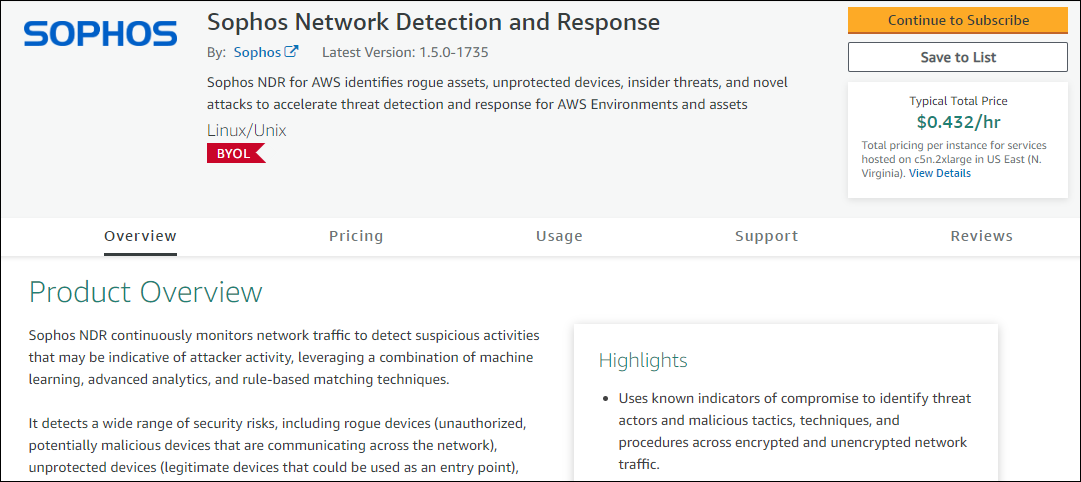
You must subscribe to NDR in the AWS Marketplace console. To do this, do as follows:
- Go to the AWS Marketplace page and find Sophos NDR.
-
On the Product Overview page, click Continue to Subscribe.
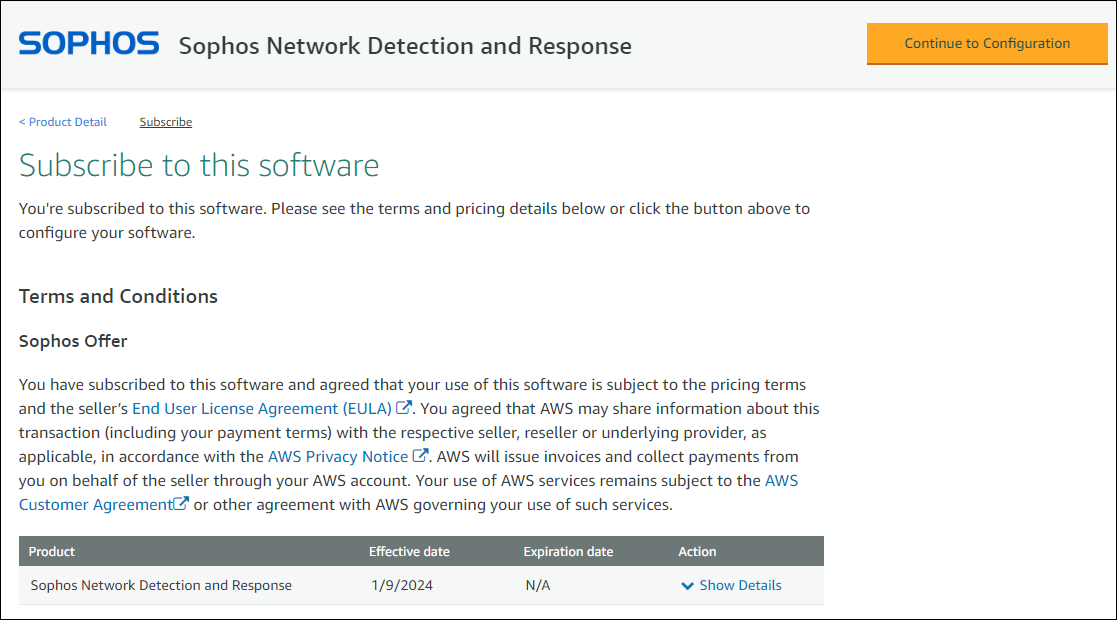
-
On the Subscribe to this software page, accept the terms and conditions and click Continue to Configuration.
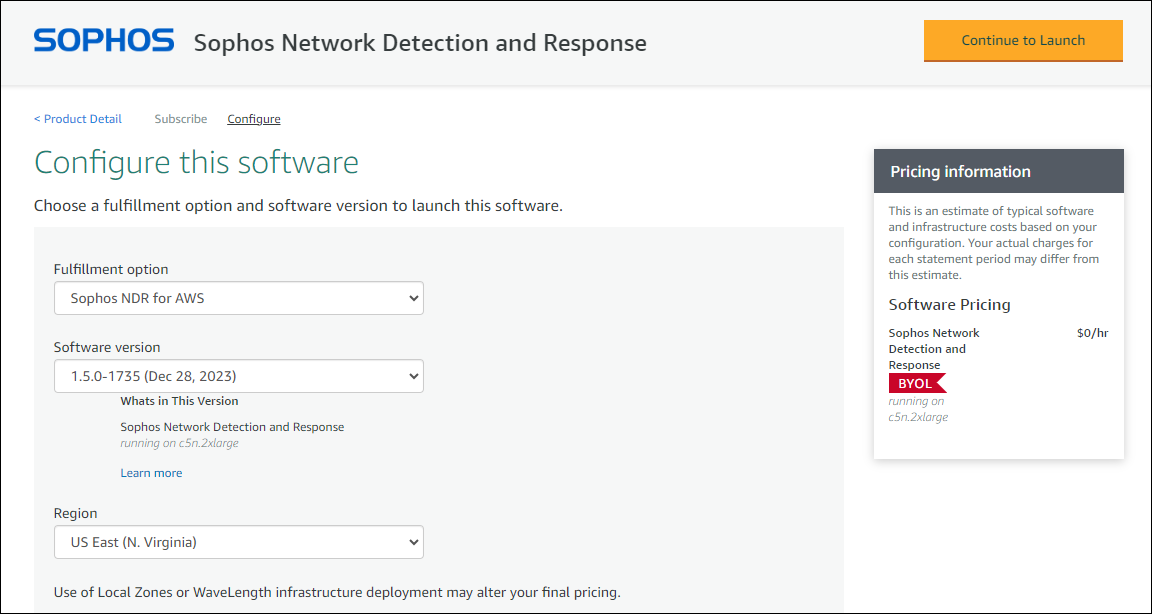
-
On the Configure this software page, check the version and region, and click Continue to Launch.
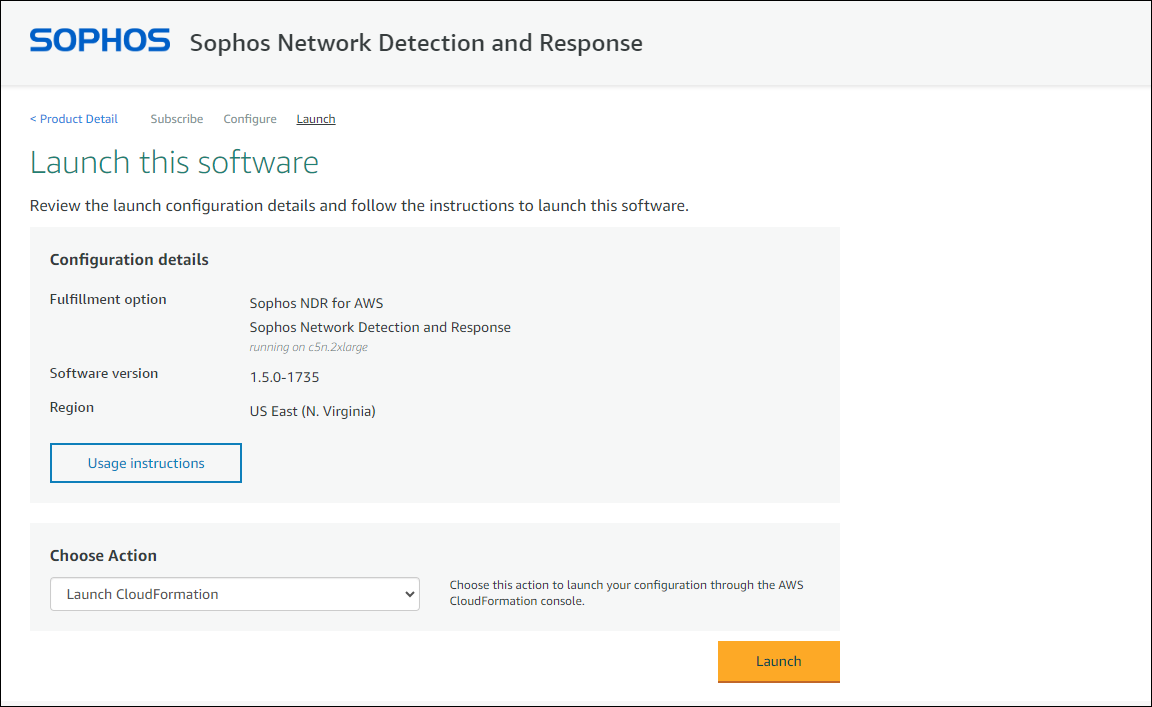
-
On the Launch this software page, click Usage instructions to see how to access Sophos Appliance Manager.
-
Click Launch.
AWS opens the Create stack page.
Create stack
Now you use the downloaded CloudFormation template to create an NDR Sensor for your AWS Account. To do this, you create a stack.
-
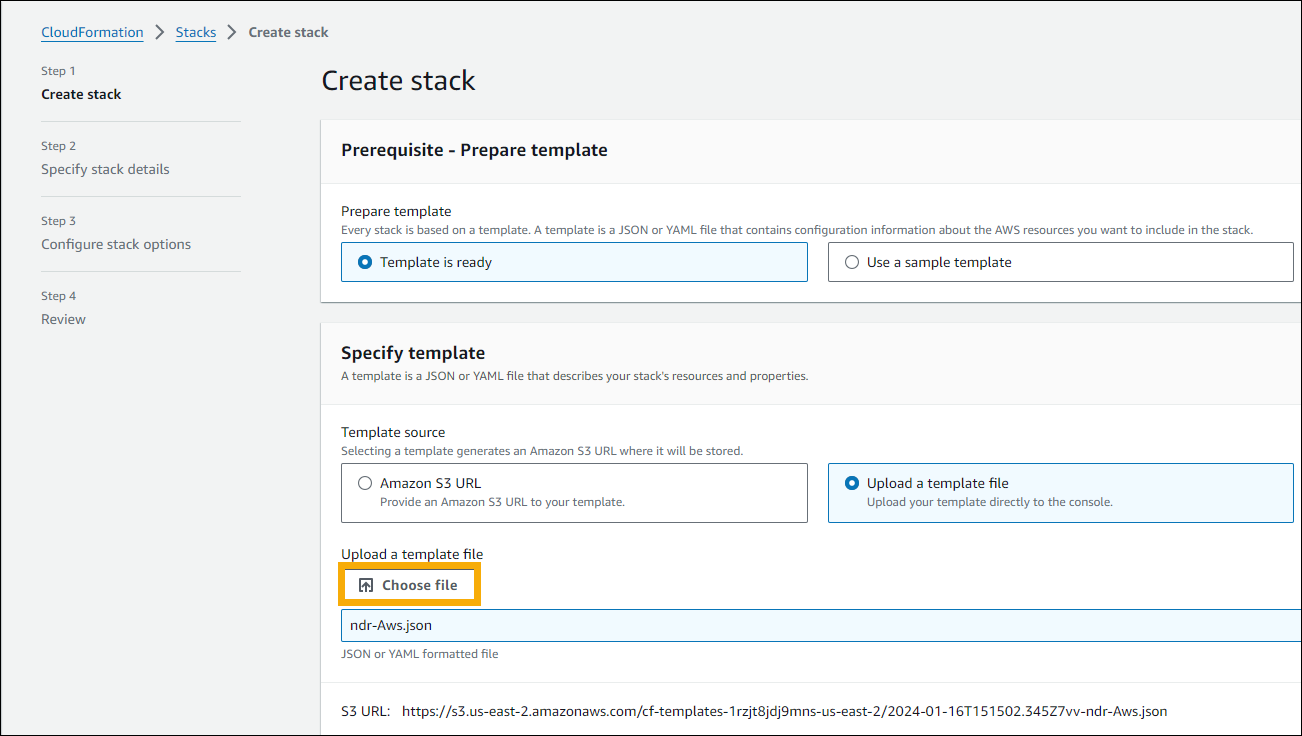
On the Create stack page, do as follows:
- Leave Template is ready selected.
- In Specify template, select Upload a template file.
- Click Choose file and select
aws_ndr_cf_latest.json. - Click Next.
-
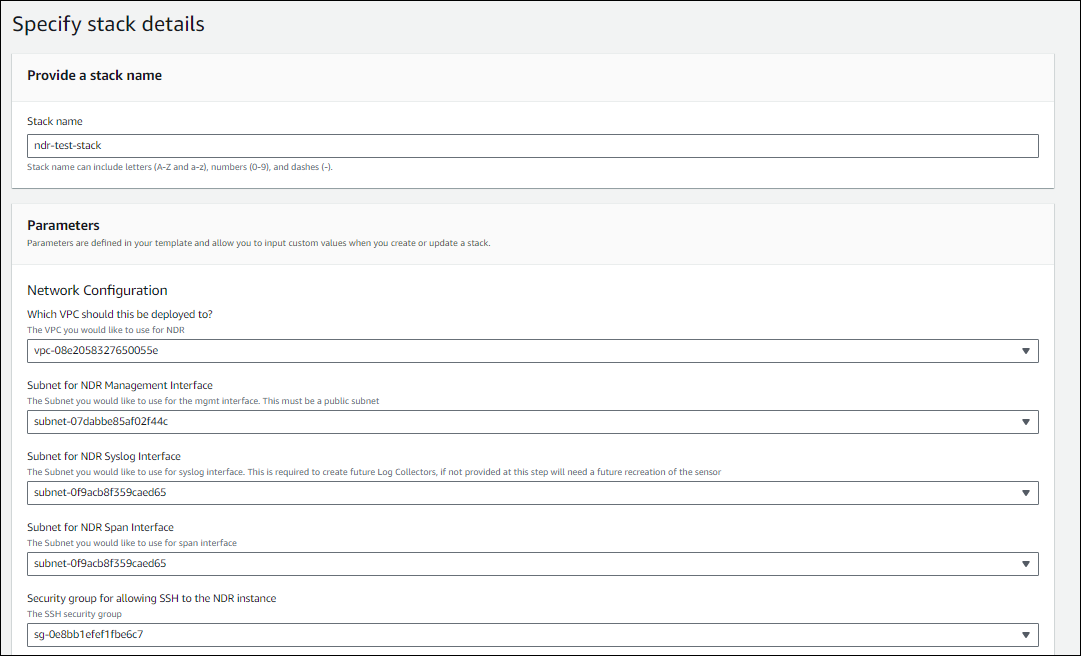
On the Specify stack details page, enter a name and the following Network Configuration details:
- An existing VPC that you want to use for NDR.
- A subnet for the NDR Management Interface. This is a public subnet.
- A subnet for the NDR syslog interface. This lets NDR attach an interface which can be used later if you add another, third-party log collector.
- A subnet for the NDR SPAN interface. The SPAN interface takes a mirrored copy of network traffic and sends it to NDR for analysis.
- The security group that gives admins SSH access to the NDR instance.
The completed network configuration details look like this example:
-
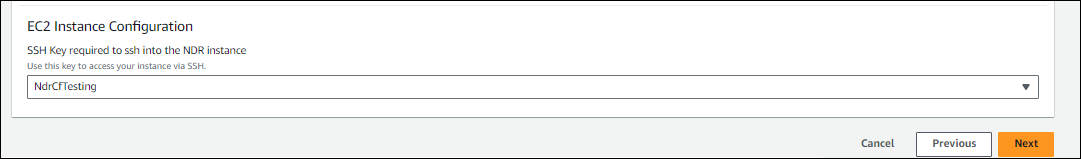
Under EC2 Instance Configuration, enter the SSH key needed to access the NDR EC2 instance, and click Next.
Note
You created and saved this SSH key pair earlier.
-
On the Configure Stack options page, accept the default AWS settings or make changes if you want to. Click Submit.
The CloudFormation template automatically chooses the right regions and AMIs based on the AWS region of the account you used to upload the template.
Wait for the NDR Sensor to be created. This can take five or six minutes.
Create a traffic mirror session
Create target mirror sessions to mirror network traffic and forward it to NDR. To do this, do as follows:
-
In AWS, go to VPC > Traffic mirror sessions > Create traffic mirror session.
-
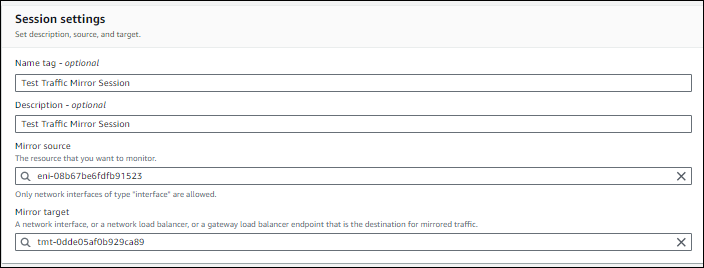
In Session settings, do as follows:
- Enter a Name Tag and Description.
- In Mirror Source, enter the network interface you want to mirror network traffic from.
- In Mirror Target, enter the SPAN interface to mirror network traffic to. Select the NDR SPAN Target that the CloudFormation template created for you.
-
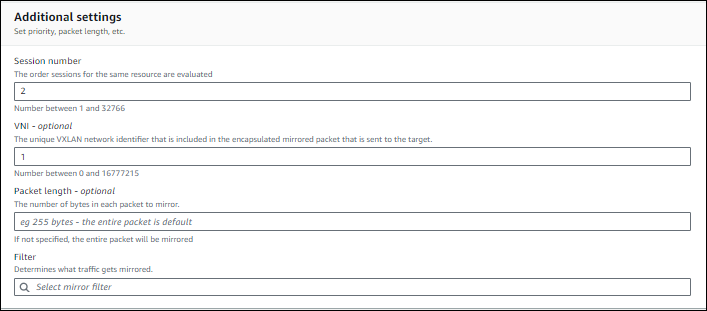
In Additional settings, do as follows:
- Enter a session number. The number decides the order in which to evaluate sessions from the same source.
- Set VNI (Virtual Network Interface) to 1.
- In Filter, select the NDR Traffic Mirror Filter that the CloudFormation template has already created.
- Click Create.
Edit the security groups
You need to edit the AWS security groups. This lets you make these changes:
- Allow syslog traffic to go to the appliance.
- Give access to Appliance Manager.
To edit security groups, do as follows:
-
In AWS, go to the Sophos NDR appliance's security details.
To do this, enter the appliance name in the AWS console search bar. When you find it, select the EC2 tab, and click the Sophos Appliance instance.
-
On the Instance Summary page, scroll down to the tabbed pages, and select the Security tab.
-
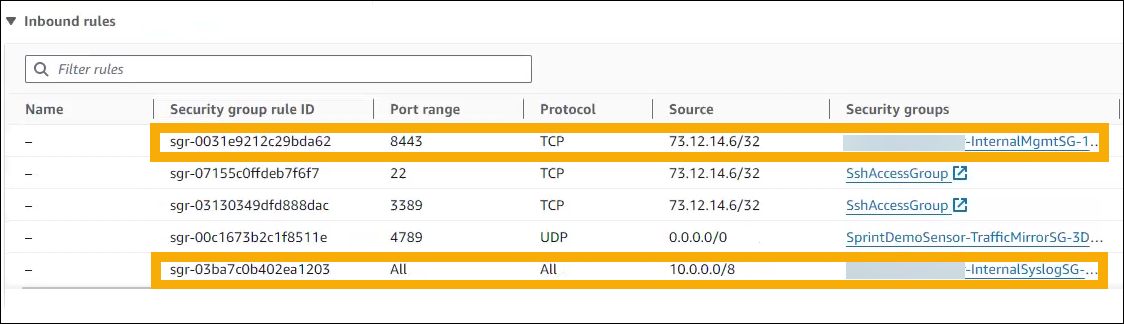
Find the
InternalSyslogSGgroup and enter the source from which you want to allow traffic for log collection. -
Find the
InternalMgmtSGsecurity group. The CloudFormation template created this for you. Add your admins to the group and give them access to port 8443 in Inbound rule.
Before you can use Appliance Manager, you also need to set a password.
Set password for Appliance Manager
The username for Appliance Manager is zadmin. To set the password, do as follows:
- In Sophos Central, go to Threat Analysis Center > Integrations > Configured.
-
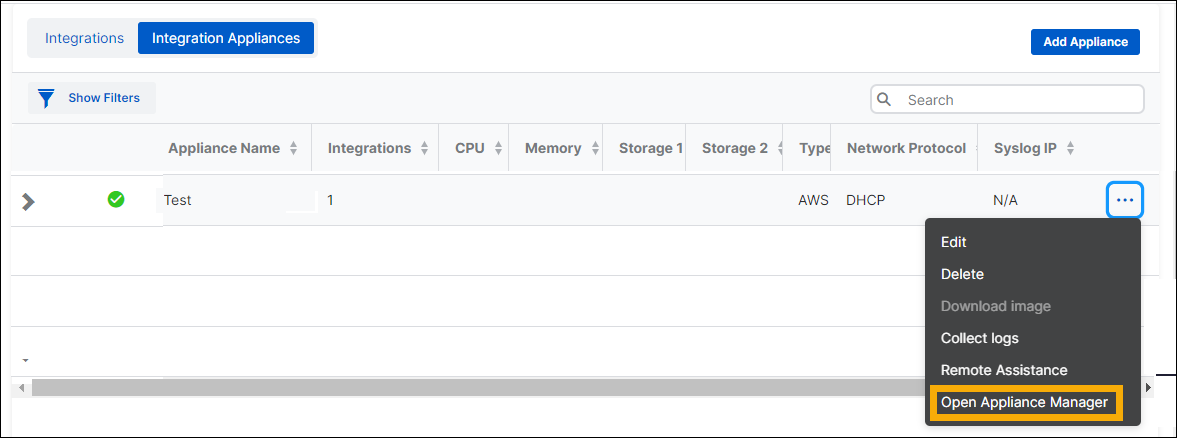
Go to the Integration Appliances tab.
-
Find your appliance. In the rightmost column, click the three dots and select Open Appliance Manager.
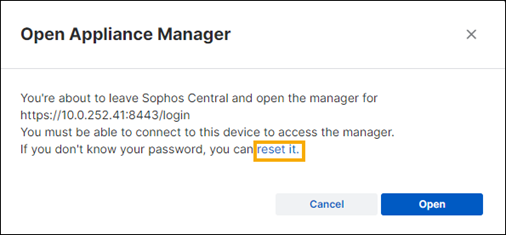
-
In the confirmation dialog, click reset it.
Any other admins who want to use Appliance Manager must also set a password.